Understanding Microsoft Defender ATP: A Comprehensive Guide
Written on
Chapter 1: Introduction to Microsoft Defender ATP
Microsoft Defender Advanced Threat Protection (ATP) is an essential security solution tailored for organizations to identify, prevent, and address sophisticated security risks. This platform enhances threat detection and prevention in conjunction with Windows Defender, the anti-malware feature of the Microsoft operating system.
Defender ATP assesses the extent of potential attacks and their likely effects, generating reports based on individual user scenarios for rapid remediation. It integrates various technologies to provide comprehensive security:
- Endpoint Behavioral Sensors: These sensors collect data on user activity on devices, transmitting it to the user's dedicated cloud environment.
- Threat Intelligence: This feature identifies known malicious tools and techniques, allowing alerts to be triggered when similar behaviors are observed.
- Cloud Security Analytics: This technology monitors diverse behaviors, aiding in formulating recommended responses to threats.
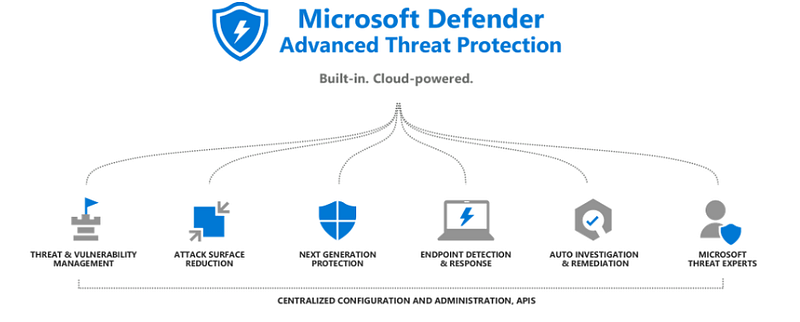
Microsoft Defender ATP offers several vital features, including:
- Threat and Vulnerability Management
- Attack Surface Reduction
- Next-Generation Protection
- Endpoint Detection and Response
- Automated Investigation and Remediation
- Expert Guidance from Microsoft Security Professionals

Chapter 2: How Microsoft Defender ATP Functions
As a cloud-based solution, Defender ATP does not require extensive deployment or infrastructure. Instead, it relies on endpoint behavioral sensors embedded in each Windows device's operating system. These sensors continuously gather data and send it to the organization's Microsoft Defender cloud instance for analysis.
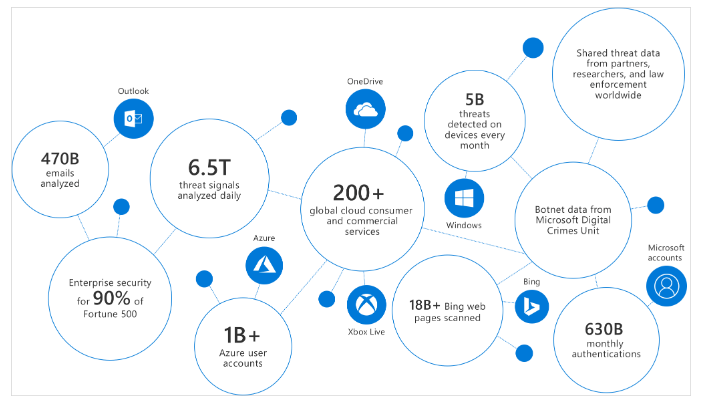
So, how does ATP identify potential threats? With millions of Windows devices in use globally, Microsoft collects a vast array of telemetry data known as the Microsoft Intelligent Security Graph. By utilizing advanced machine learning and big data analytics, Microsoft can identify patterns that may suggest malicious activity. The process begins by establishing a baseline of normal activities, which is then used to detect any anomalies. Further scrutiny of suspicious behaviors helps eliminate false positives.
The amount of data collected continues to grow daily, including information from users who have encountered threats. This data feeds into machine learning algorithms that help recognize threats across other devices, ensuring that ATP continuously evolves and learns about new threats and Indicators of Compromise (IoCs). When a legitimate threat is detected, ATP provides crucial details such as:
- Type of Threat
- Entry Point
- Potential Impact
Chapter 3: Advantages of Implementing Microsoft Defender ATP
One of the significant advantages of Microsoft Defender ATP is its minimal resource consumption, ensuring that it won’t interfere with other applications during scans. Additionally, as updates are delivered via the cloud, users experience no deployment-related issues or compatibility concerns.
The platform's automated security features provide users with timely alerts and remediation guidance within minutes. Its effectiveness has been recognized by industry leaders, including MITRE ATT&CK, Gartner, and Forrester. Key benefits include:
- Attack surface reduction to limit user vulnerabilities
- Real-time control over vulnerabilities and misconfigurations
- Various scanning options (quick, full, custom) tailored to user needs
- User-friendly interface and management, suitable for all skill levels
- Simplified endpoint management via Microsoft Intune
Chapter 4: Additional Resources
Explore security operations tools in Microsoft Defender ATP to enhance your cybersecurity measures.
Learn how to utilize MITRE ATT&CK within Microsoft Threat Protection for improved threat detection and response.